Take control of your applications and safeguard your data with a comprehensive Application Control Engine buyer’s guide.
By InvestNust
Demystify Application Control Engines! This guide explores features, benefits, considerations & more to help you choose the right ACE for your business.

These businesses in the digital world operate with a phenomenal range of applications. From productivity tools to customer relationship management (CRM) software, all applications contain sensitive data and require protection. Firewalls are not sufficient for them.
This is where an Application Control Engine enters the arena.
What is an Application Control Engine?
An ACE is a security measure that scans and regulates application activity on any network or endpoint device. It operates as a digital gatekeeper, permitting only approved applications to execute, and not the illegal ones. It helps prevent malware infection, data breach, and unapproved access.
Benefits of an Application Control Engine
Stronger Security: ACEs have a lesser chance of malware attacks and data breaches by blocking unauthorized applications.
Enhanced Compliance: ACEs can help organizations achieve industry compliance as well as support the requirements of compliance by restricting access to sensitive information.
Increased Productivity: ACEs can improve productivity and focus among employees by blocking applications unauthorized by the organization.
Reduced Operational Cost: ACEs can thus facilitate easy management of IT through the automation of application policy control.
Key Features to Consider When Choosing an ACE
Visibility and Control: Look for an ACE that allows you to gain better insight into application activity as well as provide finer control options.
Threat Detection: Select an ACE that contains in-built threat intelligence coupled with the ability to identify malicious applications and block them.
Scalability: Select an ACE that scales with your business growth.
Ease of use: There must be an intuitive user-friendly interface for managing and implementing policies related to application control.
Integration: An Ace that has the capability of integration with the existing security infrastructure.
The world of cybersecurity is always in flux, and ACEs are no exception. Peep into the future of ACEs:
Machine Learning and AI: Expect ACEs to see increased adoption of Machine Learning (ML) and Artificial Intelligence (AI). Their product will be enabled to learn the application behavior patterns, detect anomalies, and proactively block the threats ahead.
Cloud-Based Deployment: Cloud-based ACE solutions would perhaps be more in demand as it is scalable, easy to manage, and accessible.
With Zero Trust Architecture: Probably, ACEs would have a more significant working capability within Zero Trust models, hence enforcing least privilege access alongside continuous verification.
Enhancing User Experience: It would hopefully make the user interface much friendlier for users so the IT teams can easily develop as well as manage policies.
Focus on User Behavior: ACEs can be probably aligned to UEBA solutions that would analyze and track the behavior patterns of a user, and it could use them for insider threat detection.
Choosing the Right ACE for Your Business
There is one type of ACE and one size fits all. The best one that would suit your business would depend on several criteria, which may include your business size, industry, budget, and specific security requirements.
Do Your Homework:
Know your security objectives and weakness.
Do research and compare the features, prices of different ACE vendors.
Read reviews and customer testimonials for them.
Cisco ACE Application Control Engine Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
Product Overview
The Cisco ® ACE Application Control Engine Module for the Cisco Catalyst ® 6500 Series Switches and Cisco 7600 Series Routers embodies the next generation of application switches for increased availability, acceleration, and security of data center applications.
The Cisco ACE Module helps enterprises achieve four core IT application delivery goals:
- Increased application availability
- Faster application performance
- More robust data center and line-of-business application security
- More effective data center consolidation with fewer servers, load balancers, and firewalls.
The Cisco ACE Module achieves these goals by incorporating a broad set of intelligent Layer 4 load-balancing and Layer 7 content-switching technologies integrated with leading-edge acceleration and security capabilities, as shown in Figure 1. One of the important aspects of the design for Cisco ACE is its inherent virtualized architecture and role-based administration capabilities, which enable streamlining and the reduction of operational costs associated with the deployment, scalability, acceleration, and protection of applications-distinguishing features between the Cisco solution and other solutions in the marketplace.
Cisco ACE Module provides best-in-industry scalability and throughput for managing application traffic, up to 16 Gbps in a single module; up to four modules can be run in a single Cisco Catalyst 6500 Series chassis, upgradeable through software licenses or new module additions, thus providing IT with long-term investment protection and scalability.
Also, through its unique virtualization capability, Cisco ACE enables IT to provision and deliver a wide variety of multiple applications from one Cisco ACE Module that can bring high scalability for application provisioning in the data center.
To increase application availability, the Cisco ACE Module uses best-in-class application switching algorithms coupled with highly available system software and hardware.
The Cisco ACE module enhances server efficiency through highly flexible application traffic management as well as offloading CPU-intensive tasks such as SSL encryption and decryption processing, and TCP session management.
Cisco ACE is to be the last line of defense for the data center as well as applications and servers. The Cisco ACE module performs deep packet inspection that blocks malicious attacks. Highly scalable integrated security enables IT professionals to thoroughly secure high-value applications in the data center and facilitates consolidation in the data center.
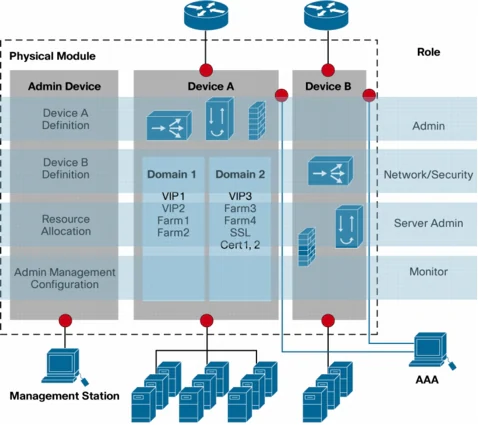
The Cisco ACE Module combines state-of-the-art application delivery features with high-performance application delivery to enhance IT efficiency and reduce TCO. Innovative features such as virtual devices, role-based administration, instant application isolation, and single-view provisioning increase IT efficiency. Improving TCO is obtained by consolidating most Layer 4 through 7 requirements into a complete and reliable application delivery platform. Vices, role-based administration, instant application isolation, and single-view provisioning. Improved TCO is accomplished by consolidating most Layer 4 through 7 requirements into a complete and reliable application delivery platform.
Source OF Information http://www.cisco.com/go/ace credit to : Cisco
Figure 1. Cisco ACE Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers

Figure 2. Cisco ACE Network Integration
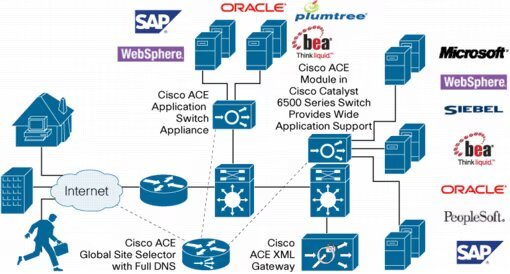
Figure 3. Cisco ACE Virtual Devices and Role-Based Administration
For More Information
For more information about the Cisco ACE, visit http://www.cisco.com/go/ace or contact your local Cisco account representative.


